CIC IoMT dataset 2024
Attack Vectors in Healthcare Devices - A Multi-Protocol Dataset for Assessing IoMT Device Security
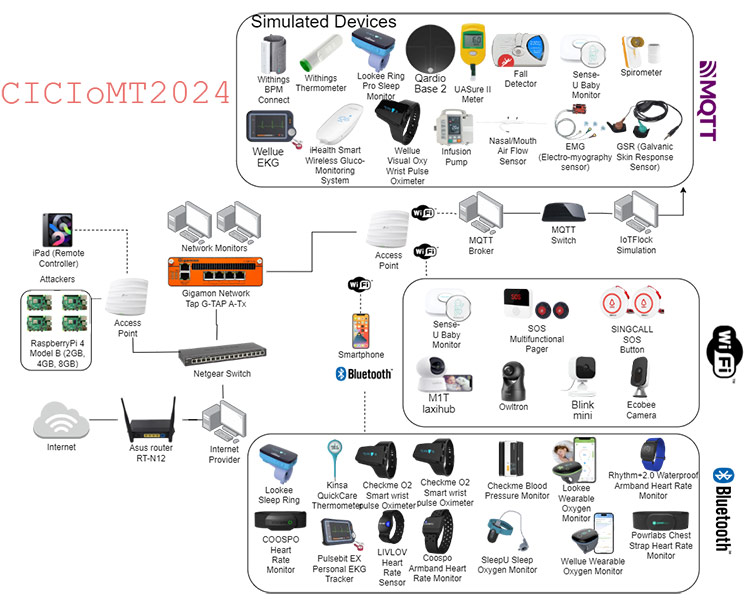
The main goal of this research is to propose a realistic benchmark dataset to enable the development and evaluation of Internet of Medical Things (IoMT) security solutions. To accomplish this, 18 attacks were executed against an IoMT testbed composed of 40 IoMT devices (25 real devices and 15 simulated devices), considering the plurality of protocols used in healthcare (e.g., Wi-Fi, MQTT and Bluetooth).
These attacks are categorized into five classes: DDoS, DoS, Recon, MQTT, and spoofing. This effort aims to establish a baseline complementary to the state-of-the-art contributions and supports researchers in investigating and developing new solutions to make healthcare systems more secure using different mechanisms (e.g., machine learning - ML).
The main contributions are:
- Development of a Comprehensive IoMT Security Dataset: In this paper we introduce the CICIoMT2024 dataset. This dataset was formed to develop a realistic benchmark for the security of healthcare devices connected to the internet i.e. Internet of Medical Things (IoMT). The dataset contains 18 different cyberattacks targeted at 40 IoMT devices and contributes to the healthcare industry by containing a diverse set of protocols that are found in many healthcare devices, namely Wi-Fi, MQTT, and Bluetooth.
- Innovative Methodology in IoMT Attack Simulation and Data Collection: An innovative approach was undertaken that simulates and captures IoMT network traffic. As healthcare organizations involve complex networks it is important to consider various cyberattack scenarios such as DDoS, DoS, Recon, MQTT, and spoofing, under a combination of real, and simulated devices. Furthermore, advanced networking tools, techniques, and hardware such as network taps ensure that the data collection is seamless, and void of interruptions.
- Profiling IoMT Device Lifecycle for Enhanced Security Understanding: The lifecycle of IoMT devices were captured in a variety of crucial phases. As mobility is commonly seen in healthcare organizations, profiling the lifecycle of IoMT devices become important in understanding the behaviours of these devices under different operational states such as power, idle, active, and interaction states. By doing so, we can understand behavioural patterns which can be used in identifying security vulnerabilities and developing better solutions.
- Multi-dimensional Evaluation: This research benchmarks the current state of ML solutions in IoMT security by evaluating the efficiency of the detection, and classification of IoMT cyberattacks using various machine learning algorithms like Logistic Regression, Adaboost, Random Forest, and Deep Neural Networks. Through this assessment, the study opens future discussions in the optimization of current algorithms, and feature engineering.


Data Description
For collecting the data, a network tap was used to capture traffic between the switch, and the Wi-Fi/MQTT enabled IoMT devices. The device provides real-time duplication of packets, and was employed to create our security, and profiling dataset.
A combination of a malicious PC, and a smartphone was used to capture malicious, and benign data for Bluetooth Low Energy (BLE) enabled devices.
The collected data are as follows:
- Wi-Fi/MQTT: A variety of attacks were performed against Wi-Fi enabled IoMT devices, and MQTT simulated devices. The attacks are as follows:
- DDos:
- SYN Flood
- TCP Flood
- ICMP Flood
- UDP Flood
- DoS:
- SYN Flood
- TCP Flood
- ICMP Flood
- UDP Flood
- Recon:
- Ping Sweep
- Vulnerability Scan
- OS Scan
- Port Scan
- Spoofing:
- MQTT:
- Malformed Data
- DoS Connect Flood
- DDoS Connect Flood
- DoS Publish Flood
- DDoS Publish Flood
- Bluetooth Low Energy (BLE): A denial of service attack was performed against BLE devices.
- Profiling: To understand the behaviours of IoMT devices in various scenarios the following experiments were conducted:
- Power: In this experiment, we powered on each device, and captured its behaviour in isolation.
- Idle: In this experiment, the whole network traffic is captured between late evening to early morning to ensure that the lab was vacant and devoid of human interactions.
- Active: In this experiment, the whole network traffic is captured. During the period of capture, fellow researchers were allowed to enter the lab, and interact with the devices to generate network traffic either passively or actively.
- Interaction: In this experiment, all possible functionalities of the IoMT devices were performed, and their corresponding network traffic was captured.
The table below showcases the obtained descriptive statistics of the features that were extracted from the collected PCAP files.
| Feature |
mean |
std |
min |
25% |
50% |
75% |
max |
| Header-Length |
29962.4717 |
282363.394 |
0 |
2.17 |
108 |
19421 |
9896704 |
| Protocol Type |
8.04720327 |
6.30483218 |
0 |
1.05 |
6 |
17 |
17 |
| Duration |
64.6369088 |
7.855306556 |
0 |
64 |
64 |
64 |
255 |
| Rate |
15744.4895 |
40008.5463 |
0 |
6.42273084 |
133.141869 |
19759.2022 |
2097152 |
| Srate |
15744.4895 |
40008.5463 |
0 |
6.42273084 |
133.141869 |
19759.2022 |
2097152 |
| fin_flag_number |
0.0051233 |
0.03415862 |
0 |
0 |
0 |
0 |
1 |
| syn_flag_number |
0.15721153 |
0.33687886 |
0 |
0 |
0 |
0 |
1 |
| rst_flag_number |
0.03951838 |
0.13929947 |
0 |
0 |
0 |
0 |
1 |
| psh_flag_number |
0.02217887 |
0.0965354 |
0 |
0 |
0 |
0 |
1 |
| ack_flag_number |
0.09566387 |
0.25214153 |
0 |
0 |
0 |
0 |
1 |
| ece_flag_number |
2.91E-06 |
0.0005036 |
0 |
0 |
0 |
0 |
0.2 |
| cwr_flag_number |
1.92E-06 |
0.00037966 |
0 |
0 |
0 |
0 |
0.2 |
| ack_count |
0.02797713 |
0.17825565 |
0 |
0 |
0 |
0 |
11.2 |
| syn_count |
0.293892 |
0.60364144 |
0 |
0 |
0 |
0 |
10.7 |
| fin_count |
0.08557531 |
0.56123908 |
0 |
0 |
0 |
0 |
151.74 |
| rst_count |
65.8712672 |
498.281211 |
0 |
0 |
0 |
0 |
9576.5 |
| HTTP |
0.00086767 |
0.0284215 |
0 |
0 |
0 |
0 |
1 |
| HTTPS |
0.00559028 |
0.06034021 |
0 |
0 |
0 |
0 |
1 |
| DNS |
0.00015156 |
0.0052478 |
0 |
0 |
0 |
0 |
1 |
| Telnet |
1.25E-05 |
0.00089169 |
0 |
0 |
0 |
0 |
0.1 |
| SMTP |
1.25E-05 |
0.00089171 |
0 |
0 |
0 |
0 |
0.1 |
| SSH |
2.61E-05 |
0.00271903 |
0 |
0 |
0 |
0 |
1 |
| IRC |
1.25E-05 |
0.00089234 |
0 |
0 |
0 |
0 |
0.11111111 |
| TCP |
0.41487102 |
0.48990278 |
0 |
0 |
0 |
0 |
1 |
| UDP |
0.31084898 |
0.45956644 |
0 |
0 |
0 |
0 |
1 |
| DHCP |
3.26E-06 |
0.00098659 |
0 |
0 |
0 |
0 |
0.6 |
| ARP |
0.00076075 |
0.019283389 |
0 |
0 |
0 |
0 |
1 |
| ICMP |
0.27351348 |
0.44404871 |
0 |
0 |
0 |
.99 |
1 |
| IGMP |
4.47E-06 |
0.0012065 |
0 |
0 |
0 |
0 |
0.7 |
| IPv |
0.99923925 |
0.01928389 |
0 |
1 |
1 |
1 |
1 |
| LLC |
0.99923925 |
0.01928389 |
0 |
1 |
1 |
1 |
1 |
| Tot sum |
636.01138 |
991.6091 |
42 |
411 |
525 |
567 |
23467 |
| Min |
55.1201614 |
69.0993765 |
42 |
42 |
50 |
54 |
1514 |
| Max |
72.3325073 |
133.609047 |
42 |
43.77 |
50 |
54 |
1514 |
| AVG |
60.5865132 |
88.0720219 |
42 |
42.0933304 |
50 |
54 |
1514 |
| Std |
6.06053694 |
38.0578569 |
0 |
0 |
0 |
0 |
721.15087 |
| Tot size |
60.5890934 |
87.8768798 |
42 |
42.24 |
50 |
54 |
1514 |
| IAT |
84683677.9 |
17819169.6 |
-1.2820613 |
84679174 |
84696417 |
84696902.6 |
169470846 |
| Number |
9.49908609 |
0.84157738 |
1 |
9.5 |
9.5 |
9.5 |
15 |
| Magnitue |
10.4382451 |
3.15807323 |
9.16515139 |
9.17497736 |
10 |
10.3923048 |
55.027266 |
| Radius |
8.56000977 |
53.8045034 |
0 |
0 |
0 |
0 |
1020.23203 |
| Covariance |
2370.54475 |
19758.8155 |
0 |
0 |
0 |
0 |
520437.887 |
| Variance |
0.09074362 |
0.2329791 |
0 |
0 |
0 |
0 |
1 |
| Weight |
141.527342 |
21.6618865 |
1 |
141.55 |
141.55 |
141.55 |
244.6 |
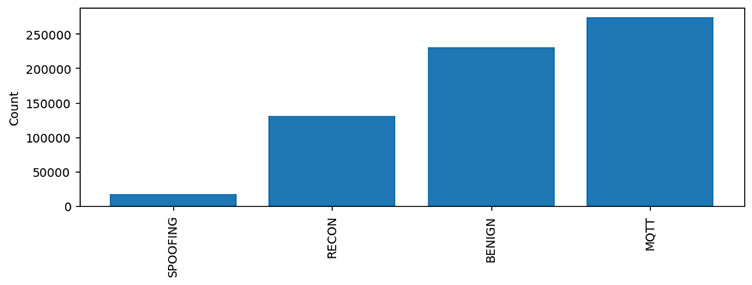
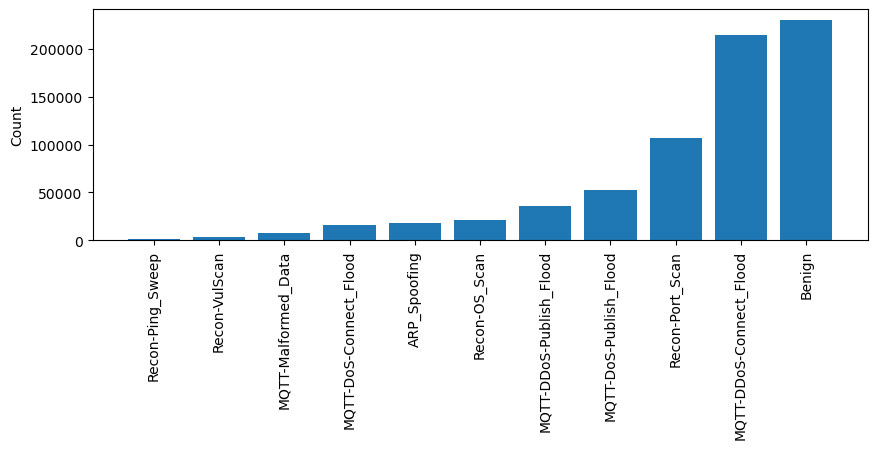
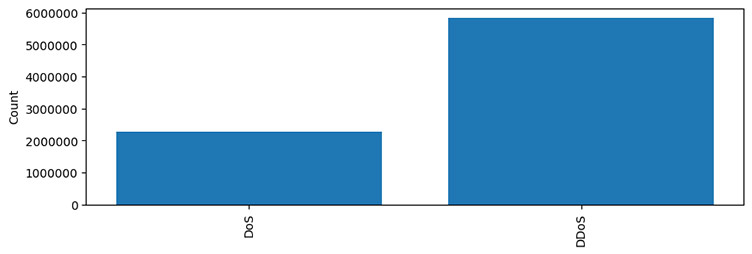
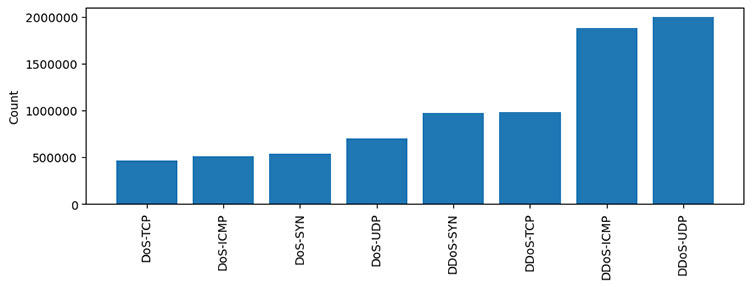
The charts below illustrate the distribution of data for each class. It can be seen that MQTT and benign traffic make up bulk of the data. In a multiclass classification, benign, and MQTT connect floods make up most of the traffic generated. Similarly, the distribution of DoS, and DDoS traffic is presented, and in a multiclass classification, UDP and ICMP DDoS floods make up the majority of the data.
Dataset Directories
The main dataset directory (CICIoMT2024) contains two subdirectories namely:
- Bluetooth: This directory includes two subdirectories namely:
- attacks: Contains the original benign, and attack Bluetooth traffic captured as .pcap files that are grouped under “test” and “train” splits.
- profiling: Contains the original profiling .pcap files. The profiling experiment that was carried out is the power experiment.
- WiFi_and_MQTT: Contains the original benign, and attack traffic performed on WiFi and MQTT enabled devices. This directory includes two subdirectories namely:
- attacks: Contains the original attack, and benign .pcap files grouped by “test” and “train” splits. This directory also includes a csv subdirectory that contains features extracted from the original .pcap files to be used in the Machine Learning (ML) evaluation (.csv files). csv files are also grouped under their respective “test” and “train” splits.
- profiling: Contains the original profiling .pcap files under various scenarios along with their respective extracted features in a csv subdirectory.
Acknowledgments
The authors would like to thank the Canadian Institute for Cybersecurity (CIC) for its financial and educational support.
Using the dataset
Webinar explanation about CIC IoT datasets: "From Profiling to Protection: Leveraging Datasets for Enhanced IoT Security" by Dr. Sajjad Dadkhah, Assistant Professor and Cybersecurity R&D Team Lead with Q&A by Sumit Kundu.
Citation
S. Dadkhah, E. C. P. Neto, R. Ferreira, R. C. Molokwu, S. Sadeghi and A. A. Ghorbani. "CICIoMT2024: Attack Vectors in Healthcare devices-A Multi-Protocol Dataset for Assessing IoMT Device Security,” Internet of Things, v. 28, December 2024.
Download the dataset






